By CRISTINA JANNEY
Hays Post
Your data is today’s gold.
Dallas Haselhorst, founder of TreeTop Security, discussed cybersecurity at the Hays Public Library on Wednesday night as he wrapped up a series of sessions to mark Cybersecurity Month.
“At the end of the day, there are a lot of people’s livelihoods that get affected adversely by getting hacked,” Haselhorst said.
Sixty percent of small business go out of business within six months of a major cyberattack, he said.
“That’s people’s jobs. That’s people feeding their families,” he said.
One misconception is that technology — anti-virus software or firewalls — will protect you from cyberattacks.
Attackers are going to go after wherever your business or home is weakest. If you are a business owner, Haselhorst suggested offering cybersecurity awareness training for your employees. At home, hackers will target the most vulnerable, too. That could be parents, kids or seniors.
“People say, ‘I don’t have anything that an attacker would possibly want,’ ” Haselhorst said. “That just couldn’t be further from the truth.”
Some of this information can include:
- Credit card and financial information
- Medical data and insurance information
- Computer resources
- Use or your email credentials
Medical data is seven times more valuable than credit card data, Haselhorst said. Credit card companies are getting exceptionally good at stopping fraud, he said. With medical data a scammer can perpetrate identity fraud, prescription fraud and insurance fraud.
You can change a credit card number, but you can’t change your Social Security number, Haselhorst noted.
Hackers can use your computer for nefarious purposes. They can use it to send ransomeware. They can use it as a jump point, which is when your computer is used to attack someone else.
“The FBI has unfortunately kicked down wrong doors before thinking someone has child pornography things on their computer,” he said.
Your email is tied to many other aspects in your life, such as resetting passwords on your bank account.
“If you think there is nothing on my computer,” he said, “there absolutely is in every single situation.”
Backups are one of the only guaranteed ways to get your information back from ransomware.
“In doing IT for the past 20-some years, one thing I can tell you is that I have seen time and time again somebody says, ‘We have backups. We have tons of backups.’ You go back and find they don’t have any backups and they haven’t been backing up for the last six months,” Haselhorst said.
Thirty-five percent of users never have backed up their data. Only 6 percent of users back up daily.
He also warned against leaving a USB drive or an external hard drive plugged into your computer. If your backup device is attached to your computer, it can be ransomwared too. Use the Cloud or disconnect your backup device.
Every day, 360,000 pieces of malware are released. Keep your devices updated. Most updates contain security updates. This includes operating systems on computers, tablets and cellphones.
Anti-virus software needs to be updated every few hours to keep up with the onslaught of malware. Browsers matter too. Haselhorst said Microsoft is no longer recommending using Internet Explorer.
Devices in the realm referred to as “the internet of things,” such as dog food feeders and surveillance systems, do not update automatically. Alexa, Google Home, a lot of the doorbells and thermostats do update automatically.
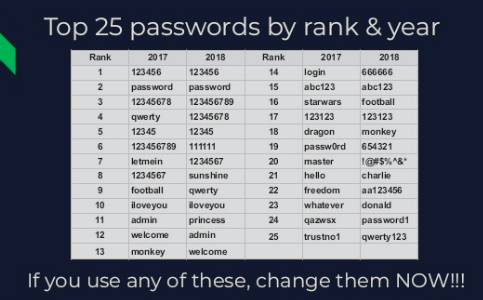
Passwords are still important to protecting your data. Don’t write down your passwords and stick them on your computer.
If you store passwords anywhere on your computer in a Word, Excel or Notepad document, these can be easily found by hackers.
You can use secure password managers, such as LastPass, KeePass and 1Password to keep your passwords safe. These applications will allow you to store all your passwords in one secure place. You unlock the program with one long password. The programs can also autofill passwords and usernames on your device.
If you use a password manager, you can use a different password for every account. If one account is compromised, that is the only data that is at risk. You can also use randomly generated passwords because you don’t have to remember them all.
“Everyone has heard about the breaches in the news. There is like a breach everyday. What happens is the systems get breached, and the hacker pulls down the password and username database,” Haselhorst said.
“What happens with that password and username data is you can get Gina’s email address and password and then I’m going to try it on Facebook. I’m going to try it on her bank account. I’m going to try it every single place I can think of that she might have an account for.”
Ninety-five percent of passwords are shared within their household. Fifth-nine percent of people use one password for all accounts.
Avoid using passwords that can easily associated with you. These include:
- Address
- Phone number
- Pet name
- Birthdate
- Sports teams
- Child’s name
Haselhorst recommends passwords of 16 to 18 characters. Length is more effective than complexity. He suggested using password phrases, such as MysonwasbornNovember1995! versus P@ssw0rd.
Haselhorst discussed ways to keep you safe from malicious links. These included verifying the link, hovering over the link, giving it the sniff test and finally clicking if it passes all of the previous three tests.
You may receive an email from someone you know, but red flags could be in the subject line, strange wording, an odd signature or a strange link, especially those outside of the U.S. To hover, let your cursor rest on the link without clicking. This will show where the link is actually going to take you.
Hackers can have a link that says anything in the text of an email or text, but it may take you to a completely different site. If there are numbers in the URL instead of letters, don’t trust it, Haselhorst said.
Scammers will also try to use condensed links to hide where they are really taking you. You can use www.linkexpander.com to find the expanded address.
You can also receive links through SMS messages. Is the message expected and from someone you trust? You can “hover” on a tablet or cell phone with a prolonged press on the link.
Scammers will also use a sense of urgency both online and over the phone to get you to click on links or had over sensitive information. Companies like Apple and Microsoft are never going to call or email you personally, Haslehorst said, although scammers are using their names.
Ninety-two percent of all malware is delivered by email. Stop and think before you click on attachments. Are you expecting the email? Are you expecting the attachment? Don’t enable editing if macros have been disabled.
Scammers will also using “phishing” or “whaling” to create a targeted attack. Haselhorst gave the example of a scammer using the name of the CEO of a company to send an email to the CFO of a company asking him or her to set up an illegitimate vendor or account. The scammer then asks the CFO to deposit money in the bogus account.
When individuals are targeted, scammers might ask for gift or prepaid credit cards or financial information. Technical safeguards are not effective in stoping these scam.
“These are emails. This is text,” Haselhorst said. “There is nothing on the planet that is going to stop these things except who is sitting in a chair. Somebody is going to have to think about that.”
Robocalls continue to be an epidemic in this country. Remember scammers can make the number look like it is coming from your local area. If you have any question about who you are talking to, hang up and call back on a published number.
Other general security tips include use caution when attaching phones or other devices to your computer that could infect your computer with malware. Be careful of WiFi hotspots and avoid public computers.
Haselhorst also noted even trusted websites can be hacked and be hosting malware.
You can contact TreeTop Security at www.treetopsecurity.com or 785-370-3444.